- The same level of access for all employees
- Access level division
- A complex approach to cybersecurity
Two months ago, the world was braced for developed countries to cope with the threat of coronavirus. Although quarantine measures have had an effect, and the peak of the pandemic has passed, we must keep thinking about security. In an attempt to safeguard the employees’ health by transferring them to remote work, the business faces a new threat – the risk of cybersecurity breaches.
In the current market conditions, the demand for IT services is growing, and business is interested, first of all, in automation and organization of remote work. The crisis stimulates the development of technology and, at the same time, opens new opportunities for attackers. It’s an obvious point that the corona crisis will cause an explosive increase in information leaks, fraud, industrial espionage, which will result in large financial losses for companies.
The transformation and development of such directions as IoT, Industry 4.0, FinTech, MedTech, AI/ML, and VR will increase the quality and life expectancy and provide each of us with opportunities for personal growth. However, the development of these technologies will bring threats to the security of personal and corporate data. New vulnerabilities in software, hardware, and processes will be discovered.
The remote work format is our new reality. Many companies are already optimizing processes with the help of remote work and will continue the development in this direction after the abolition of restrictions.
In order to fulfill their duties when working remotely, employees often need access to confidential information and internal services of the company. It seems that we already have all the necessary technologies that allow organizing a comfortable remote work (VPN, VDI, BYOD Policies, 2FA, endpoint security solutions), but now there is a need to look at them from a different perspective. It is necessary to combine these technologies different ways and adapt them to new processes.
Although ready-made solutions initially adapted to modern threats are already entering the market, few companies apply these solutions and do the utmost to protect their data. Due to the specifics of our work, we often meet companies where even basic IT-security hygiene principles are not implemented.
Let’s consider several options for organizing the remote work of employees.
The same level of access for all employees
In this case, if any employee is compromised, an attacker gains access to all information systems in the organization. The risk of information leakage is very high. This risk increases when working from home, as the user is in a poorly controlled environment, surrounded by smart kettles, vacuum cleaners, light bulbs. The user’s workplace can be accessed by those who are unfamiliar with the regulations (children, pets).
Let’s consider several options for organizing the remote work of employees.
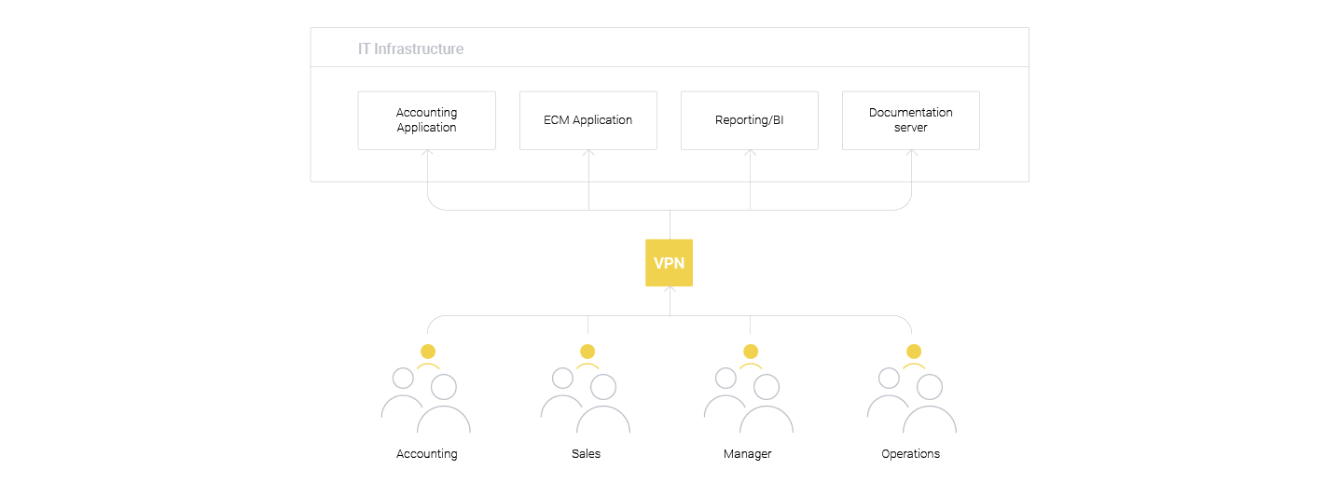 Such an organization scheme is often found in small companies, but the risks associated with the leakage of confidential information can be critical for businesses of all sizes.
Such an organization scheme is often found in small companies, but the risks associated with the leakage of confidential information can be critical for businesses of all sizes.
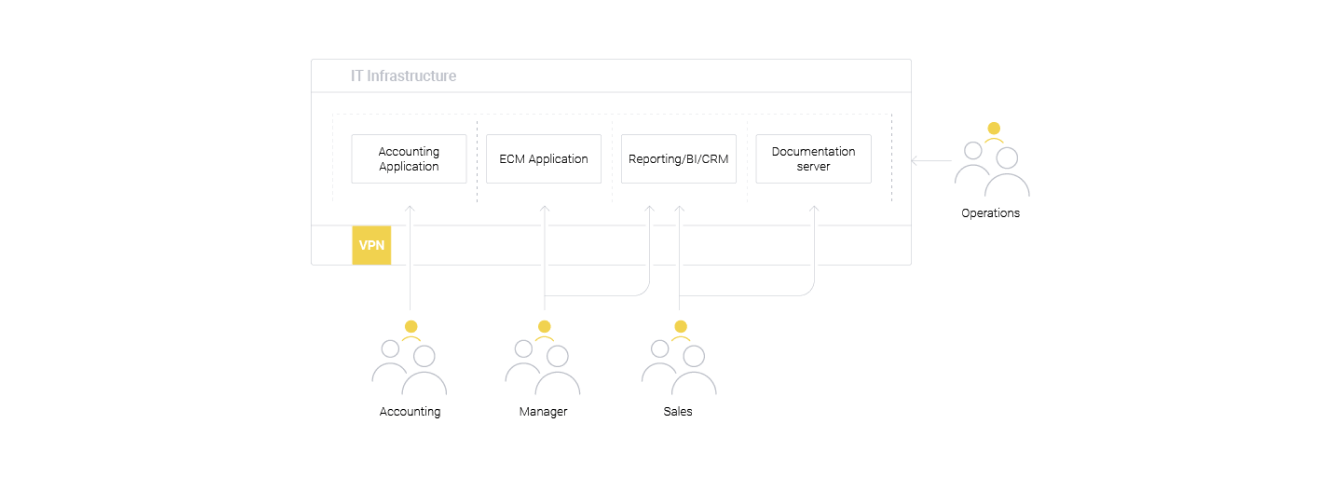
Access level division
More responsible organizations are building their systems with a greater granularity of access rights. Each user belongs to a certain group and has access only to resources necessary for the performance of their official duties.
If a user account is compromised, it is more difficult for an attacker to gain access to all information and gain a foothold in the system. This reduces the risks, but usually, for an experienced hacker, gaining access to all information is just a matter of time.
A complex approach to cybersecurity
As an example, let’s consider a large company that has a responsible attitude towards security.
The company has taken the following measures:
- Overhauled their security in the context of their industry, e.g. media and entertainment cyber security, finance security, etc.
- Increased granularity of user roles
- Configured two-factor authentication
- Uses additional information security systems
- All working devices are protected with endpoint security
- Information is securely encrypted
- All necessary events from information systems for incident investigation are collected
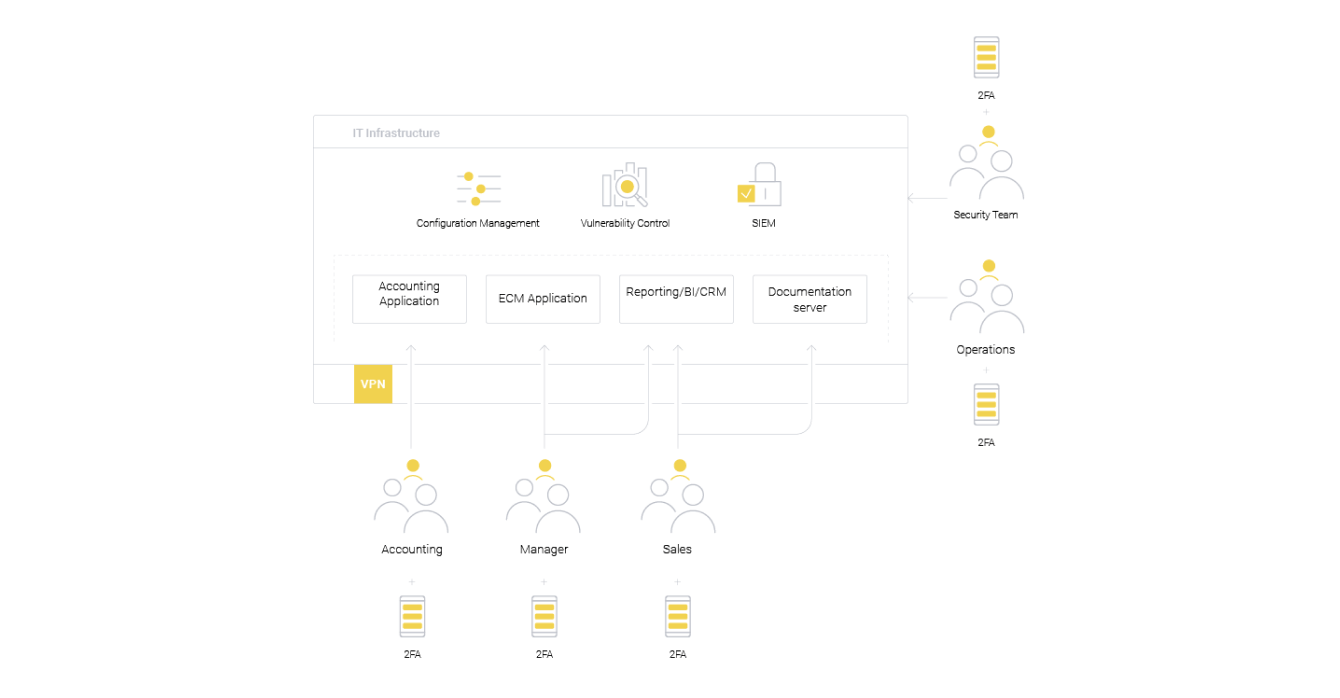 It is worth mentioning that companies with such an approach to information security often have a cumbersome infrastructure, which is why some basic information security rules can be ignored. Configuration errors and outdated software that can be cracked appear. Security Team, together with the Operations Team, are not always able to promptly make changes and apply updates.
It is worth mentioning that companies with such an approach to information security often have a cumbersome infrastructure, which is why some basic information security rules can be ignored. Configuration errors and outdated software that can be cracked appear. Security Team, together with the Operations Team, are not always able to promptly make changes and apply updates.
However, in such infrastructures, it is also more difficult for an attacker to gain a foothold in the network – the available time online can be measured in minutes. With a strict time limit, an attacker will try to download the maximum amount of information, and not seek out something necessary for their purposes. In this case, information systems, information security systems, and infrastructure can be designed using AI/ML technologies that, according to a number of criteria, will determine abnormal behavior within a short time and prevent unauthorized access to data. Information systems may have the ability to encrypt downloaded data or block access to downloads on the fly, allowing only viewing certain sections of data through applications.
This is the future that has already come.
When working with a customer, we assess the needs of the business and bottlenecks, optimize the cost of solutions, and offer relevant services. Dear colleagues, friends, partners! Please, wash your hands and follow the IT security hygiene.





