- The most common targets for SDV attacks
- Mobile apps
- Malware
- Server
- Software
- Autonomous systems
- How to ensure robust cybersecurity in SDVs
- Compliance with legislation
- GDPR requirements
- Authentication
- Cybersecurity audits
- Electronic control units
- Open-source components
- To sum up: SDV security is non-negotiable
Software in vehicles has long become their integral part. Modern cars are connected, cloud-based, and personalized. While appealing to car owners, these features rely substantially on knowing the user. Thus, they pose risks to the security of their sensitive information. What threats should the drivers be aware of, and what measures must manufacturers take to ensure the ultimate security?
The most common targets for SDV attacks
A few years ago, when the first Teslas came to the European market, the question on everyone’s lips was: “Is it possible that my personal information is shared with other parties I’m unaware of?” Although this threat didn’t prove true, there are parts of SDVs that frequently become targets of attackers.
Mobile apps
In the past five to six years, mobile phones have become increasingly integrated with vehicle infotainment systems. Popular car makers offer dedicated mobile apps to remotely control cars, from locking and unlocking them and setting the climate to buying new features and scheduling maintenance appointments. Sadly, these apps can become access points to personal information.
Malware
This can be disguised as music files for the vehicle’s MP3 player or installed via unsecured or outdated Bluetooth protocols.
Server
In SDVs, key management systems and certificates are closer to a server than a car. In case an attacker gets hold of a server, they potentially gain access to connected apps, transactional information, operational features, an OBD-II port, etc.
Software
Since it’s regularly updated, chances are that hackers can act through these over-the-air updates. Automakers must also pay close attention to the reliability of open-source software providers, as tier-ones and suppliers almost always rely on open source.
Autonomous systems
Though artificial intelligence and machine learning in cars are still in their infancy, it’s evident that their usage will only increase. Already today, gen AI enables natural interaction with the vehicle’s infotainment system through voice control. What’s more, AI can control navigation and the contact list. In XPENG’s MONA M03 vehicles, AI controls ADAS. It’s expected that in the future, AI will be communicating with the vehicle-to-everything infrastructure to adapt the ADAS to the situation created by the V2X. AI and ML will also ensure reliable SDV performance in low-connectivity areas by learning which features the driver is using and what their usual routes are, and being able to get them the content before they need it.
As we see these advancements coming from Chinese OEMs, major OEMs in Europe, such as Volkswagen Group, BMW, Mercedes, and Daimler, will also implement AI to keep up with the competition. At this, AI implementation challenges cybersecurity in vehicles in various ways.
How to ensure robust cybersecurity in SDVs
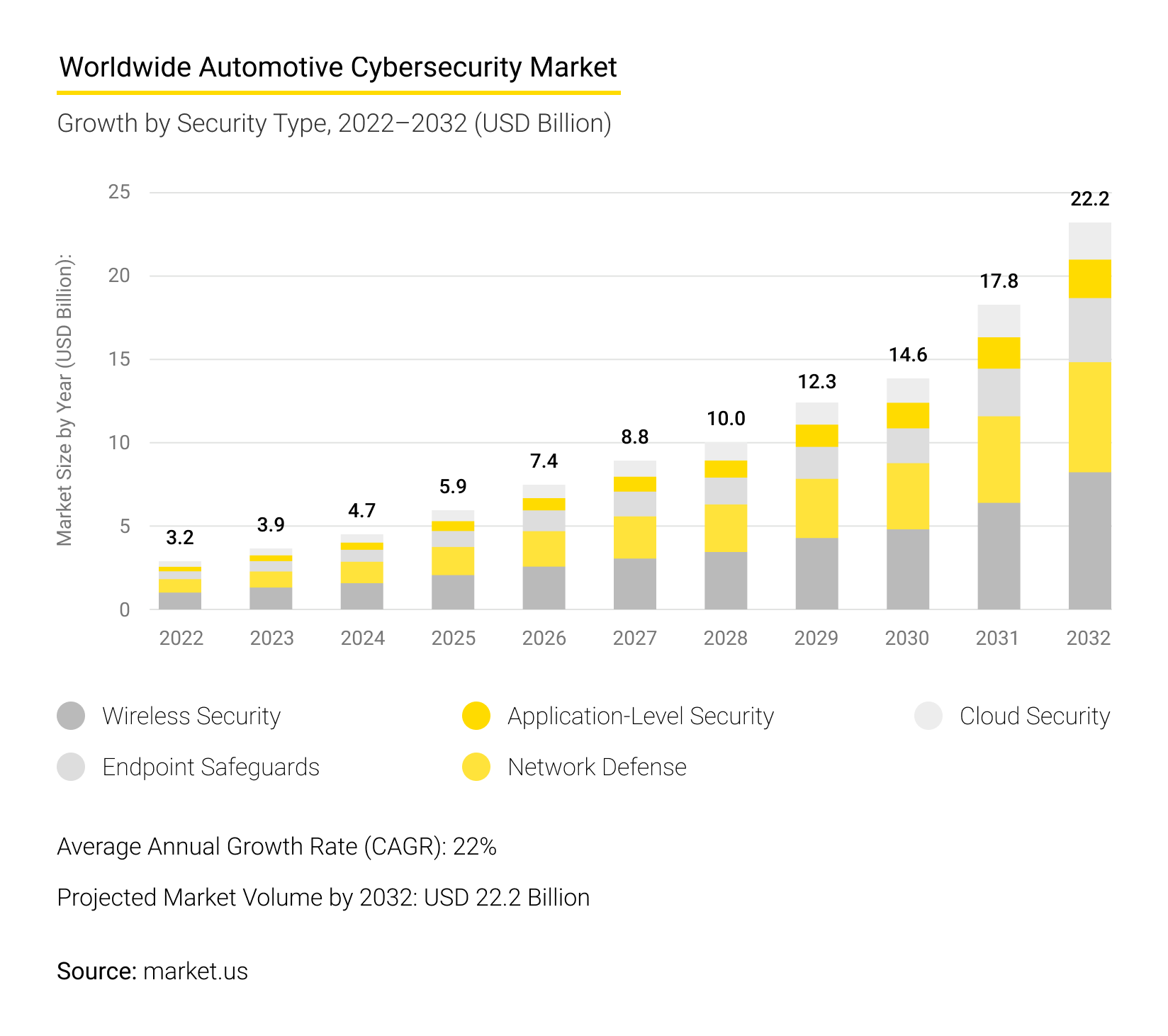
Only a few years ago, vehicle security barely existed, and hacking a vehicle was much easier than it is now. Today, security is a priority in automotive. Below are the aspects of SDVs that automakers take special care of when ensuring cybersecurity.
Compliance with legislation
Cybersecurity measures in automotive are stipulated in the ISO/SAE 21434:2021 norm and the R155 regulations by the United Nations Economic Commission for Europe (UNECE). Automakers should take cues from multinational companies and governments and apply the same work ethic to their operations.
GDPR requirements
The port of defense number one is normally GDPR. Car makers should ensure that end users are aware of what personal information they’re sharing, how it will be used, and that they consent to it.
Authentication
Much of the processing power used by manufacturers now goes toward encryption. Features like authentication are increasingly required, even within the vehicle itself, where services must be verified before use.
Cybersecurity audits
A dependable IT company can verify software robustness by conducting penetration testing, auditing access management, implementing secure updates, and more.
Electronic control units
Centralization and consolidation of hardware have been strong trends in automotive over the past decade. The number of ECUs managing climate control, fuel delivery, braking systems, and sensor-based detection has reduced from a hundred-plus to fewer and fewer. This is beneficial for security, as fewer microchips are vulnerable to attacks. ECU security can be reinforced through protected data storage, intrusion detection mechanisms, and hardware-based acceleration for cryptography.
Open-source components
The use of open-source components in SDVs is inevitable, particularly since there's no need to reinvent the wheel each time. Often, the problem is around liability. Open-source software doesn’t have support that goes with it. At the same time, there are companies that work with it and provide support modules around it.
Most cryptographic algorithms are open-source, demonstrating that open-source software from reputable sources can be highly secure. Its transparency allows anyone to review the code and try to break it. When issues are found, they are typically disclosed and addressed publicly, enabling developers to respond quickly. In contrast, with closed-source software, if someone discovers a vulnerability, there's less incentive to report it, and they might exploit it for personal gain.
To sum up: SDV security is non-negotiable
By 2029, SDVs are expected to account for 90% of all vehicle production. It’s no wonder that the V2X cybersecurity market is projected to increase at a CAGR of 12.3% through 2032. As the industry shifts toward SDVs, cybersecurity has become a cornerstone upon which the future of automotive is established. This can be achieved by relying on the robust expertise of accomplished IT partners.